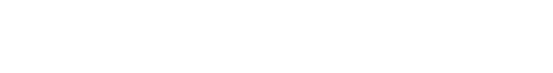Since December 2018, Electrum Bitcoin wallet users have been under siege by a persistent phishing campaign, resulting in losses totaling 771 BTC (around $4 million). Malwarebytes Labs uncovered the scheme, revealing that hackers exploited a software vulnerability to deceive users into downloading a fake version of the Electrum wallet.
In response, Electrum’s developers took an unusual step in February. They leveraged the same software flaw to redirect users towards downloading the latest, patched version of the wallet.
However, the situation escalated in March when a new vulnerability emerged. Developers then initiated what they called a “counter-attack,” essentially targeting vulnerable clients to prevent them from connecting to malicious servers.
Adding to the turmoil, a botnet launched Distributed Denial of Service (DDoS) attacks against Electrum’s servers. This malicious action aimed to disrupt the service and isolate users with outdated wallets, making them even more susceptible to the ongoing phishing attacks.
Why Electrum Became a Target
Electrum wallet, known as a “lightweight” Bitcoin wallet, utilizes a method called Simplified Payment Verification (SPV). This allows users to transact without downloading the entire Bitcoin blockchain (hundreds of gigabytes in size). Instead, Electrum operates in a client-server model. The user’s wallet (client) connects to a network of peers to verify transactions.
While generally secure, this approach has a vulnerability: anyone can run a public Electrum peer. As the graph demonstrates, the number of active Electrum peers has risen significantly. This open nature created an opportunity for attackers to set up malicious peers and exploit the system.
Malicious wallets
Malwarebytes identified two distinct malicious Electrum wallets, labeled “Variant 1” and “Variant 2,” indicating the involvement of different actors and a potentially longer history of this campaign predating December 21, 2018.
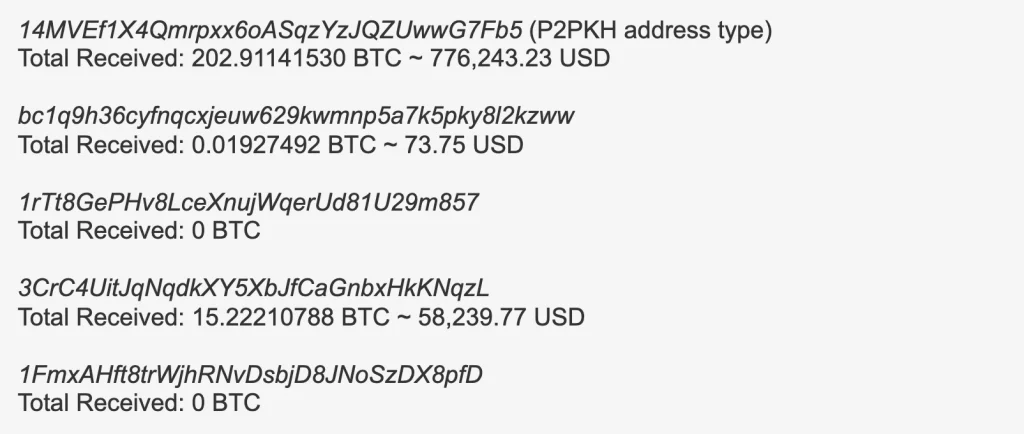
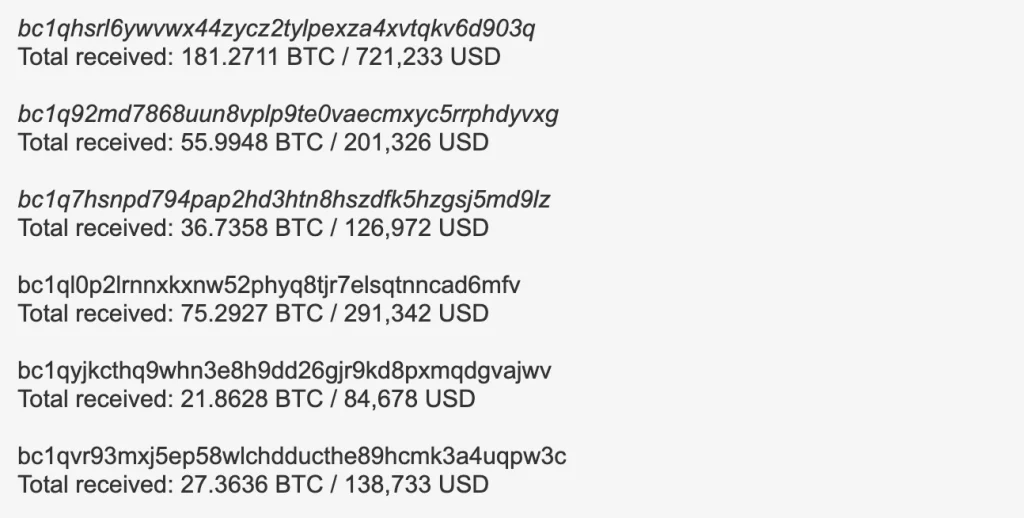
Variant 1 stands out due to its data exfiltration capabilities. Stolen wallet keys and seed data were uploaded to a remote server using obfuscated code hidden within an unusual file named “initmodules.py.” Additionally, any existing balance in the compromised wallet was automatically transferred to one of several pre-determined addresses controlled by the attackers. The choice of destination address depended on the victim’s Electrum wallet address format, with Pay-to-PubkeyHash (P2PKH) being the primary target, suggesting a focus on users with default settings.
Variant 2 employed a more aggressive strategy, leading to a higher amount of stolen Bitcoin compared to Variant 1. Instead of redirecting victims to a malicious GitHub site, it utilized a domain name closely resembling the official Electrum download site, increasing the deception’s effectiveness.
The attackers demonstrated a deep understanding of Electrum’s code and functionalities. They deactivated auto-updates, eliminated confirmation prompts, and even disabled Replace-by-Fee (RBF) transactions. This latter feature, introduced later in Bitcoin’s development, allows users to create a double-spend transaction, potentially reversing the theft if they were aware of its existence and acted quickly. By disabling RBF, the attackers ensured the stolen funds could not be easily recovered.
Tracing the Stolen Funds
Analysis of blockchain transactions revealed that Variant 1 dispersed the stolen Bitcoin into smaller amounts, primarily in chunks of 3.5 BTC and 1.9 BTC. This pattern suggests a money laundering technique called “smurfing,” where funds are broken down into smaller deposits to avoid triggering Currency Transaction Reports (CTRs) which are typically required for transactions exceeding $10,000.
Future Threats and Mitigation
Malwarebytes researchers predict the likelihood of future attacks, highlighting the attackers’ determination and the financial success of this campaign. The researchers emphasize the ongoing “vicious cycle” where malicious actors continue to disrupt legitimate Electrum nodes and promote fake updates through phishing attempts.
To mitigate these threats, users running Electrum servers are strongly advised to:
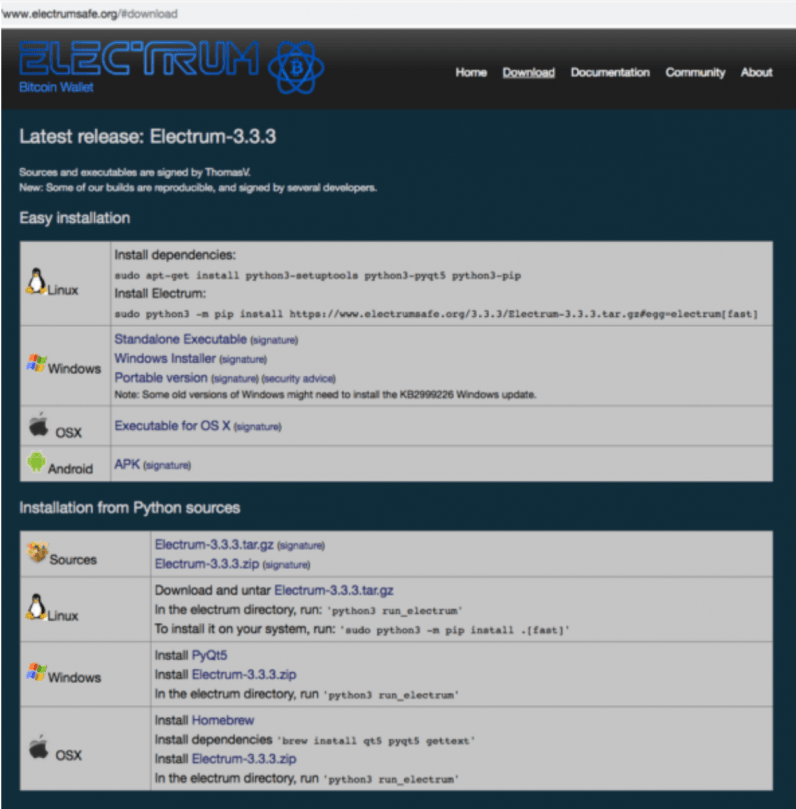
- Update to the latest version (3.3.4) from the official repository.
- Remain vigilant and cautious of warning messages that may be disguised phishing attempts.
- Consider additional security measures to protect their Electrum wallets.