Electrum, a popular Bitcoin wallet, is currently under siege from a large-scale and sophisticated cyberattack. Users are urged to exercise extreme caution when using the platform until the issue is fully resolved.
The attack involves a vast botnet, consisting of over 140,000 compromised machines, which is bombarding Electrum’s servers with Denial-of-Service (DoS) attacks. The attackers’ aim is to disrupt the legitimate service and redirect users to malicious versions of the Electrum software specifically designed to steal Bitcoin.
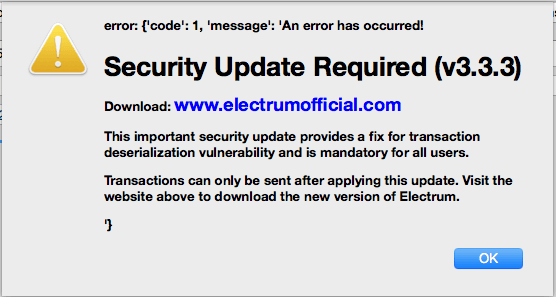
Worryingly, the attackers have also deployed numerous servers hosting these compromised versions of the Electrum client. If a user unknowingly synchronizes their vulnerable Electrum wallet with one of these malicious servers (hundreds have been identified so far), they are prompted to “update” their client with the hacked version.
A security researcher close to the situation has revealed to Hard Fork that installing these fake versions of Electrum leads to immediate loss of all funds held in the old, legitimate wallets.
The financial impact of this attack is severe, with millions of dollars worth of Bitcoin already stolen. In one instance, a single individual lost nearly $140,000. The DoS attacks themselves represent an escalation, having only begun about a week ago. Community-run servers have reported being bombarded with traffic exceeding 25 Gigabits per second.
Electrum users should be prepared for potential service interruptions as administrators work tirelessly to mitigate the damage caused by this intense influx of malicious traffic.
“We are hopeful to resolve this issue within the coming hours or days,” lead Electrum developer Thomas Voegtlin shared with Hard Fork.
Did New Security Measures Trigger the Electrum Attack?
The Electrum community has been grappling with a persistent Bitcoin phishing problem for months.
The notorious “electrumstealer” Trojan horse and its variants are believed to have already siphoned millions of dollars worth of Bitcoin from unsuspecting users.
While there’s no definitive link between this ongoing phishing campaign and the recent DoS attack, the latest assault appears to specifically target users running outdated Electrum clients.
Our source explained that developers had implemented modifications to key Electrum servers in an attempt to mitigate exposure to the phishing scam. This action, they speculate, may have triggered the attackers to launch such a large-scale DoS attack against Electrum’s infrastructure.
“With the legitimate servers incapacitated by the attack, there’s a heightened risk of users connecting to the malicious ones,” the source warned. “The initial versions of the attack exploited a vulnerability in the Electrum wallet by using modified Electrum servers to send deceptive messages prompting users to ‘upgrade’ to a malicious version. These attacks were initially countered by leveraging Google’s Safe Browsing service to block access to these malicious sites for potential victims.”
The attackers are proving to be persistent, with over 200 domains currently identified as hosting the Electrum malware, such as “electrumx.network.” Unfortunately, blacklisting these malicious servers has become less effective due to the delay in Google updating its Safe Browsing database.
Lead developer Voegtlin explained that a patch had been previously implemented to automatically take outdated, vulnerable Electrum wallets offline as soon as a connection to a legitimate server was established (Electrum requires 8-10 connections for full functionality).
“The attacker’s motives remain unclear; it could be a form of retaliation following the steps we took last month to prevent phishing attacks,” Voegtlin commented. “This counter-measure has proven effective against phishing because it doesn’t require numerous legitimate servers; if you randomly connect to 10 servers, the chances are high that at least one of them is implementing the counter-attack.”
Voegtlin added, “Since deploying the counter-attack, we haven’t received reports of any recent successful phishing attempts.” This highlights the ongoing cat-and-mouse game between Electrum developers and the attackers, with each side adapting their tactics in response to the other.
Users with Outdated Electrum Clients Face Highest Risk
Electrum currently lacks an auto-update feature, leaving users vulnerable if they haven’t manually upgraded their clients to the latest version. This means users who downloaded Electrum long ago and haven’t updated since are at the highest risk, as emphasized by Voegtlin.
“Updated versions are not vulnerable to the phishing attack,” Voegtlin clarifies, “but the service itself might experience temporary disruptions. In such cases, we recommend users stick to the same server (disable auto-connect) until they successfully establish a session.”
He further explains, “While the attackers may attempt to disrupt legitimate servers to facilitate their phishing campaign, they require more than just a user connecting to their server. They need a vulnerable client to connect exclusively to their servers, which is significantly less likely.”
Therefore, to ensure safety, users are strongly urged to only download Electrum software from the official domain or its GitHub repository. Installing and updating Electrum clients exclusively from these sources is the primary defense against these attacks.
Electrum developers are actively working on a related patch to further enhance security. Additionally, users are encouraged to run their own servers, as a larger number of legitimate public Electrum servers helps dilute the impact of such attacks.